Information Systems Security Architecture Professional (ISSAP) Exam Dumps


Information Systems Security Architecture Professional
The CISSP-ISSAP is an appropriate credential if youre a chief security architect or analyst. Typically, you work as an independent consultant or in a similar capacity.
As the architect, you play a key role in the information security department. Your responsibilities fall between the C-suite and upper managerial level and the implementation of the security program.
Although your role is tied closely to technology, it may be closer to the consultative and analytical process of information security.
This security architect certification proves your expertise developing, designing and analyzing security solutions. It also shows you excel at giving risk-based guidance to senior management in order to meet organizational goals.
Elevate your knowledge and skills even higher as a go-to expert in information security architecture.
The Ultimate Guide to the CISSP-ISSAP covers everything to know about this elite and specialized certification. See how the CISSP-ISSAP concentration builds on the CISSP and helps you design the next level of your career.
Exclusive features
- Is the CISSP-ISSAP Right for Me-
- CISSP-ISSAPs from Around the Globe
- Fast Facts About CISSP-ISSAP
- Benefits of Being CISSP-ISSAP-Certified
- Benefits of (ISC)2 Membership
- CISSP-ISSAP Exam Overview
- Official CISSP-ISSAP Training
- Pathway to CISSP-ISSAP Certification
- Free CPE Opportunities
- Certification is Just the Beginning

ISC2
ISSAP
Information Systems Security Architecture Professional
https://killexams.com/pass4sure/exam-detail/ISSAP
environment the customer will not even know the main database server is down.
Clustering also provides load balancing. This is critical for Web servers in high volume
e-commerce situations. Clustering allows the load to be distributed over many
computers rather than focused on a single server.
QUESTION: 240
Drag and drop the appropriate DRP (disaster recovery plan) documents in front of their
respective functions.
Answer:
162
Explanation:
The different types of DRP (disaster recovery plan) documents are as follows: Executive
summary: It is a simple document which provides a high-level view of the entire
organization's disaster recovery efforts. It is useful for the security managers and DRP
leaders as well as public relations personnel who require a non-technical perspective on
the disaster recovery effort. Department-specific plan: It helps the IT personnel in
refreshing themselves on the disaster recovery procedures that affect various parts of the
organization. Technical guide: It helps the IT personnel in getting the alternate sites up
and running. Checklist: It helps critical disaster recovery team members in guiding their
actions along with the chaotic atmosphere of a disaster.
QUESTION: 241
Which of the following is the most secure method of authentication?
A. Smart card
B. Anonymous
C. Username and password
D. Biometrics
Answer: D
Explanation:
Biometrics is a method of authentication that uses physical characteristics, such as
fingerprints, scars, retinal patterns, and other forms of biophysical qualities to identify a
user. Nowadays, the usage of biometric devices such as hand scanners and retinal
scanners is becoming more common in the business environment. It is the most secure
method of authentication. Answer option C is incorrect. Username and password is the
least secure method of authentication in comparison of smart card and biometrics
authentication. Username and password can be intercepted. Answer option A is
incorrect. Smart card authentication is not as reliable as biometrics authentication.
Answer option B is incorrect. Anonymous authentication does not provide security as a
user can log on to the system anonymously and he is not prompted for credentials.
QUESTION: 242
Which of the following are the phases of the Certification and Accreditation (C&A)
process? Each correct answer represents a complete solution. Choose two.
A. Detection
B. Continuous Monitoring
C. Initiation
D. Auditing
163
Answer: C, B
Explanation:
The Certification and Accreditation (C&A) process consists of four distinct phases:
1.Initiation
2.Security Certification
3.Security Accreditation
4.Continuous Monitoring
The C&A activities can be applied to an information system at appropriate phases in the
system development life cycle by selectively tailoring the various tasks and subtasks.
Answer options D and A are incorrect. Auditing and detection are not phases of the
Certification and Accreditation process.
QUESTION: 243
Which of the following cryptographic algorithm uses public key and private key to
encrypt or decrypt data ?
A. Asymmetric
B. Hashing
C. Numeric
D. Symmetric
Answer: A
Explanation:
Asymmetric algorithm uses two keys, public key and private key, to encrypt and decrypt
data.
QUESTION: 244
Sonya, a user, reports that she works in an electrically unstable environment where
brownouts are a regular occurrence. Which of the following will you tell her to use to
protect her computer?
A. UPS
B. Multimeter
C. SMPS
D. CMOS battery
Answer: A
Explanation:
164
UPS stands for Uninterruptible Power Supply. It is a device that provides uninterrupted
electric power even after power failure. When a power failure occurs, the UPS is
switched to the battery provided inside the device. It is used with computers, as power
failure can cause loss of data, which has not been saved by a user. Answer option C is
incorrect. Switch Mode Power Supply (SMPS) is a device that converts raw input power
to controlled voltage and current for the operation of electronic equipment. SMPS uses
switches for high efficiency. Answer option D is incorrect. Complimentary Metal Oxide
Semiconductor (CMOS) is a chip installed on the motherboard, which stores the
hardware configuration of a computer.
QUESTION: 245
Your company is covered under a liability insurance policy, which provides various
liability coverage for information security risks, including any physical damage of
assets, hacking attacks, etc. Which of the following risk management techniques is your
company using?
A. Risk acceptance
B. Risk avoidance
C. Risk transfer
D. Risk mitigation
Answer: C
Explanation:
Risk transfer is the practice of passing risk from one entity to another entity. In other
words, if a company is covered under a liability insurance policy providing various
liability coverage for information security risks, including any physical damage of
assets, hacking attacks, etc., it means it has transferred its security risks to the insurance
company. Answer option B is incorrect. Risk avoidance is the practice of not performing
an activity that could carry risk. Avoidance may seem the answer to all risks, but
avoiding risks also means losing out on the potential gain that accepting (retaining) the
risk may have allowed. Answer option D is incorrect. Risk mitigation is the practice of
reducing the severity of the loss or the likelihood of the loss from occurring. Answer
option A is incorrect. Risk acceptance is the practice of accepting certain risk(s),
typically based on a business decision that may also weigh the cost versus the benefit of
dealing with the risk in another way.
QUESTION: 246
Della works as a security manager for SoftTech Inc. She is training some of the newly
recruited personnel in the field of security management. She is giving a tutorial on DRP.
She explains that the major goal of a disaster recovery plan is to provide an organized
way to make decisions if a disruptive event occurs and asks for the other objectives of
the DRP. If you are among some of the newly recruited personnel in SoftTech Inc, what
165
will be your answer for her question? Each correct answer represents a part of the
solution. Choose three.
A. Guarantee the reliability of standby systems through testing and simulation.
B. Protect an organization from major computer services failure.
C. Minimize the risk to the organization from delays in providing services.
D. Maximize the decision-making required by personnel during a disaster.
Answer: B, C, A
Explanation:
The goals of Disaster Recovery Plan include the following : It protects an organization
from major computer services failure. It minimizes the risk to the organization from
delays in providing services. It guarantees the reliability of standby systems through
testing and simulation. It minimizes decision-making required by personnel during a
disaster.
QUESTION: 247
You work as a Network Consultant. A company named Tech Perfect Inc. hires you for
security reasons. The manager of the company tells you to establish connectivity
between clients and servers of the network which prevents eavesdropping and tampering
of data on the Internet. Which of the following will you configure on the network to
perform the given task?
A. WEP
B. IPsec
C. VPN
D. SSL
Answer: D
Explanation:
In order to perform the given task, you will have to configure the SSL protocol on the
network. Secure Sockets Layer (SSL) is a protocol used to transmit private documents
via the Internet. SSL uses a combination of public key and symmetric encryption to
provide communication privacy, authentication, and message integrity. Using the SSL
protocol, clients and servers can communicate in a way that prevents eavesdropping and
tampering of data on the Internet. Many Web sites use the SSL protocol to obtain
confidential user information, such as credit card numbers. By convention, URLs that
require an SSL connection start with https: instead of http:. By default, SSL uses port
443 for secured communication. Answer option B is incorrect. Internet Protocol Security
166
(IPSec) is a method of securing data. It secures traffic by using encryption and digital
signing. It enhances the security of data as if an IPSec packet is captured, its contents
cannot be read. IPSec also provides sender verification that ensures the certainty of the
datagram's origin to the receiver. Answer option A is incorrect. Wired Equivalent
Privacy (WEP) is a security protocol for wireless local area networks (WLANs). It has
two components, authentication and encryption. It provides security, which is equivalent
to wired networks, for wireless networks. WEP encrypts data on a wireless network by
using a fixed secret key. WEP incorporates a checksum in each frame to provide
protection against the attacks that attempt to reveal the key stream. Answer option C is
incorrect. VPN stands for virtual private network. It allows users to use the Internet as a
secure pipeline to their corporate local area networks (LANs). Remote users can dial-in
to any local Internet Service Provider (ISP) and initiate a VPN session to connect to
their corporate LAN over the Internet. Companies using VPNs significantly reduce long-
distance dial-up charges. VPNs also provide remote employees with an inexpensive way
of remaining connected to their company's LAN for extended periods.
QUESTION: 248
The security controls that are implemented to manage physical security are divided in
various groups. Which of the following services are offered by the administrative
physical security control group? Each correct answer represents a part of the solution.
Choose all that apply.
A. Construction and selection
B. Site management
C. Awareness training
D. Access control
E. Intrusion detection
F:Personnel control
Answer: A, B, F, C
Explanation:
The administrative physical security control group offers the following services:
Construction and selection Site management Personnel control Awareness training
Emergency response and procedure Answer options E and D are incorrect. Intrusion
detection and access control are offered by the technical physical security control group.
QUESTION: 249
Jasmine is creating a presentation. She wants to ensure the integrity and authenticity of
the presentation. Which of the following will she use to accomplish the task?
A. Mark as final
B. Digital Signature
167
C. Restrict Permission
D. Encrypt Document
Answer: B
Explanation:
Digital signature uses the cryptography mechanism to ensure the integrity of a
presentation. Digital signature is an authentication tool that is used to ensure the
integrity and non-repudiation of a presentation. It is used to authenticate the presentation
by using a cryptographic mechanism. The document for a digital signature can be a
presentation, a message, or an email.
168
For More exams visit https://killexams.com/vendors-exam-list
Kill your exam at First Attempt....Guaranteed!
Killexams has introduced Online Test Engine (OTE) that supports iPhone, iPad, Android, Windows and Mac. ISSAP Online Testing system will helps you to study and practice using any device. Our OTE provide all features to help you memorize and practice test questions and answers while you are travelling or visiting somewhere. It is best to Practice ISSAP Exam Questions so that you can answer all the questions asked in test center. Our Test Engine uses Questions and Answers from Actual Information Systems Security Architecture Professional (ISSAP) exam.
At killexams.com, we always suggest that you download the ISSAP exam Question Bank for a trial run. Go through the questions and answers before you apply for the full version. Killexams.com allows you to receive 3 months of free updates for ISSAP Information Systems Security Architecture Professional (ISSAP) exam questions. Our certification group consistently works at the backend to update the ISSAP Question Bank as needed.
If you are determined to pass the ISC2 ISSAP exam and secure a highly paid position, consider registering at killexams.com. Many professionals are actively gathering actual ISSAP exam questions, which you can access for your preparation. You will receive Information Systems Security Architecture Professional (ISSAP) exam questions that guarantee you to pass the ISSAP exam, and every time you download, they will be updated with 100% free of charge. While there are other companies that offer ISSAP Exam Questions, the legitimacy and up-to-date nature of ISSAP PDF Questions is a significant concern. To avoid wasting your time and effort, it's best to go to killexams.com instead of relying on free ISSAP Exam Questions on the internet. The primary objective of killexams.com is to help you understand the ISSAP course outline, syllabus, and objectives, allowing you to pass the ISC2 ISSAP exam. Simply reading and memorizing the ISSAP course book is insufficient. You also need to learn about difficult and tricky scenarios and questions that may appear in the actual ISSAP exam. Thus, you should go to killexams.com and download free ISSAP PDF sample questions to read. Once you are satisfied with the Information Systems Security Architecture Professional (ISSAP) questions, you can register for the full version of ISSAP cheat sheet at a very attractive promotional discount. To take a step closer to success in the Information Systems Security Architecture Professional (ISSAP) exam, download and install ISSAP VCE exam simulator on your computer or smartphone. Memorize ISSAP Exam Questions and frequently take practice tests using the VCE exam simulator. When you feel confident and ready for the actual ISSAP exam, go to the test center and register for the actual test. Passing the real ISC2 ISSAP exam is challenging if you only rely on ISSAP textbooks or free Question Bank on the internet. There are numerous scenarios and tricky questions that can confuse and surprise candidates during the ISSAP exam. That's where killexams.com comes in with its collection of actual ISSAP braindumps in the form of Exam Questions and VCE exam simulator. Before registering for the full version of ISSAP Question Bank, you can download the 100% free ISSAP PDF Questions. You will be pleased with the quality and excellent service provided by killexams.com. Don't forget to take advantage of the special discount coupons available.
ISSAP dumps, ISSAP braindumps, ISSAP Questions and Answers, ISSAP Practice Test, ISSAP Actual Questions, Pass4sure ISSAP, ISSAP Practice Test, Download ISSAP dumps, Free ISSAP pdf, ISSAP Question Bank, ISSAP Real Questions, ISSAP Cheat Sheet, ISSAP Bootcamp, ISSAP Download, ISSAP VCE
I purchased EC dumps from the Internet and found killexams.com. They provided me with several cool materials to prepare for the exam, and I was able to pass it without any problems.
Martha nods [2023-6-9]
I am ecstatic to have passed my ISSAP cert exam with a score of 97%. The killexams.com exam simulator and study material were crucial to my success. Thank you!
Martin Hoax [2023-5-21]
killexams.com acted as my captain or pilot, guiding me towards success in my ISSAP exam. Their guidelines and support helped me observe the right direction, ultimately leading me to achieve glory. I will forever be grateful to this online test center for their invaluable assistance.
Lee [2023-4-16]
More ISSAP testimonials...


![]()

2: Shared Origins, diverse Roads
assistance SHEETThe 2nd Temple as increased by means of Herod
First-century Jerusalem became dominated by way of the huge expansions to the Temple Mount begun by Herod the terrific in 20 BCE and never completed except presently before the outbreak of the great riot in sixty six CE. massive protecting walls had been developed to double the plateau on appropriate of the Mount to forty acres. The Antonia Fortress (named for Mark Antony) guarded the northwest corner of the Mount, the place it become most vulnerable to assault. A bridge over the Tyropeaen Valley, whose end factor is marked today via Wilson’s Arch, authorized direct access to the Temple Mount from the upper city. Robinson’s Arch, in the southwest nook of the Temple Mount, supported stairs up from the decrease metropolis. Most pilgrims, however, would gain entry to the Temple Mount by the use of the splendid southern staircase. lots of the city, including the Temple Mount, was destroyed by using Roman legions in 70 C.E. today’s Western Wall, a remnant of Herod’s retaining wall, is discovered between Wilson’s and Robinson’s Arches.
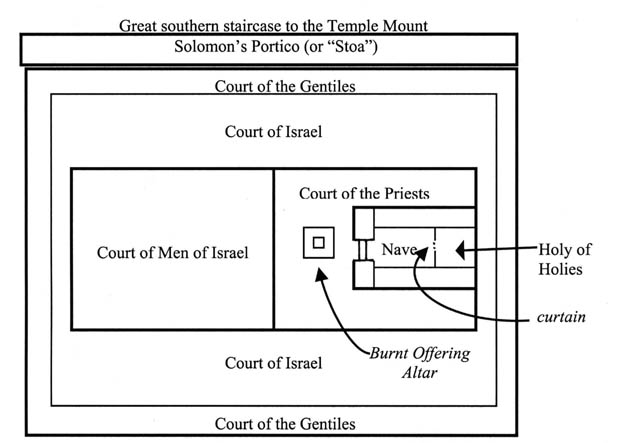
despite the fact there are numerous identifications for the courtyards, the design of constructions and walls is pretty neatly based
Temple Liturgies
The essential ritual that took region within the Temple was sacrifice. Sacrifice in the Hebrew/Jewish culture became the offering of flowers or animals to God. Blood was regarded to be a purifying, lifestyles-energizing liquid that become the vessel of God’s ruach or Spirit. The ritual use of blood could establish or restore or reinvigorate relationships. Wealthier people were expected to latest more effective offerings. terrible americans could provide birds and even flour. Entrance to the Temple precincts required ritual purity and as one moved into its inner courts entry grew to become greater restrained. Ritual purity required cleanliness and the absence of bodily emissions so as to draw as regards to the divine presence. The Holy of Holies could best be entered by the excessive Priest annually on Yom Kippur.
kinds of Sacrifices provided within the Temple
Burnt providing or Holocaust
This turned into a sacrifice wherein an animal or bird become slain, skinned, and cleaned as if for a meal, after which burned completely on the burnt-offering altar. The flame and smoke of the offering rising toward heaven changed into viewed as existence being absolutely given back to God. This ritual declared that all things belonged to God. It was the holiest of all sacrifices.
Peace offering
during this sacrifice only part of the animal changed into burned on the altar to God. The relaxation of the meal become taken to be eaten via the priest and the offerer. This sacrifice become provided to praise or thank God, to meet some promise made by means of the offerer, or to set up a covenant among two or greater people and God.
Sin or Guilt offering
In these sacrifices, no meat would be back to the offerer to eat. half changed into burned for God, and the priest took the relaxation. Blood from the sacrifice changed into rubbed on the altar and poured round its base to show that life with God turned into being restored.
The Showbread
This became an providing of twelve desserts of nice flour. These would be authorised by using the priests every Sabbath and placed on a desk in the nave of the Temple. Incense or fragrance presented with the cakes can be burned on the incense altar. The twelve desserts signified the covenant between God and the twelve tribes of Israel.
The Three Pilgrimage gala's
Passover (Pesach)
in the first-century, Passover memorialized the Exodus from Egypt. although particulars are sketchy it is likely that in 2d Temple times a seven-day pageant turned into celebrated which started with the slaughtering of lambs in the Temple. The meat turned into then consumed via families all over a meal that included unleavened bread (matzah) and bitter herbs.
Pentecost (Shavuot or Weeks)
happening fifty days after Passover, this feast may additionally have initially marked the conclusion of the grain harvest. In 2nd Temple instances it celebrated God’s gift of the Torah to Moses on Mount Sinai. It become hence a covenant renewal feast and maybe turned into observed with a ceremony comparable to that described in Exodus 24:three-eight.
Tabernacles (Sukkot or cubicles)
The eight-day feast originated as an autumnal harvest competition and have become associated with prayers for rain. For seven mornings, a solemn procession went to the spring of Gihon to the southeast of the Temple Mount where a priest crammed a golden pitcher with water. Then the procession returned up to the Temple carrying branches (paying homage to temporary shacks used in the container right through harvest time) and lemons or citrons symbolizing the harvest. The men processed around the burnt offering altar while the priest poured the water through a silver funnel from the altar onto the floor under. On the seventh day, the altar turned into circled seven instances. On the first night, and perhaps the others as smartly, 4 colossal golden candlesticks, topped through golden bowls by which floated wicks made from the girdles of the priests, have been lighted in the court of Israel. It became mentioned that each one Jerusalem basked in the easy that shone from the courtroom.
The Ministry of Jesus
The phrase "Kingdom [or Reign] of God" appears to be a particular phrase of Jesus, youngsters the theory of God's kingly rule looks often in Israel's scriptures. All his deeds and phrases seem to stream from the conviction that God's rule over the earth become starting:
certain beliefs emerged among Jesus' Jewish followers after experiencing him as "raised." Their setting up concepts set the foundations for what would turn into a separate non secular neighborhood.
In raising Jesus, God has given divine approval of every thing Jesus did and pointed out.
therefore, the Reign of God have to certainly be starting up as Jesus had pointed out. His exaltation is the first of a series of predicted hobbies that should be about to happen:
the restoration of Israel (e.g., Acts 1:6)
the extension of salvation to the Gentiles (an expectation confirmed when preaching about Jesus is warmly welcomed by means of Gentile "God-fearers")
the general resurrection of all of the useless (see Matthew 27:51-fifty three)
Communities of those that believed that the Crucified One had been exalted bring together. They seek to be united in radical equality and love, experiencing the new lifetime of the Spirit of the Raised Lord.
with a view to understand why a crucifixion sufferer became the agent of God’s plans, the scriptures of ancient Israel were scoured for perception and read in exceptional techniques. The suffering servant songs in Isaiah and Psalm 22 provided exceptionally fruitful texts.
Jesus, the celestially-enthroned Lord, the first fruits of the useless, has the divine power of judgment. he'll soon return in triumph to mete out justice and to establish the Reign of God (e.g., 1 Thessalonians 4:13-5:eleven; Mark 14:62; Acts three:19-21).
Jesus followers started to sing and pray about him at their carrying on with fellowship meals as the unique Lord and Son of God.
widespread aspects of Rabbinic Judaism (as put in writing by means of the rabbis within the centuries after the destruction of the 2d Temple)
Prayer, the efficiency of God's instructions (mitzvot), and the analyze of the Torah deliver holiness, the forgiveness of sins, and constitute an acceptable sacrifice to the Lord. These activities substitute the Temple sacrificial equipment as the skill to access God.
spiritual observances increasingly ensue within the context of the family unit and the home. The pilgrimage festivals are tailored to a non-Temple context.
Questions and commentaries, and responses to different's solutions and comments, develop into the primary activity of the rabbis. A constructing body of written knowledge and reflection is still composed right down to the current day.
major Rabbinic Texts
The Mishnah ("oral instructing") changed into compiled and edited round 200 C.E. in Sepphoris within the Galilee. Understood because the first written expression of the "oral law" that had circulated among some Jews for a long time, it's a group of laws and ethics prepared in six sections or "orders." The orders are subdivided into "tractates," totaling sixty-three tractates in the Mishnah as a whole.
The Midrash is produced from homiletic, theological, moral, and criminal expositions of the bible composed across the identical time as the Mishnah and Gemara.
The Gemara ("completion") contains rabbinic texts that expound upon the Mishnah. In a extensive sense, the Mishnah and Gemara together make up the Talmud or Oral law, which is regarded to have the equal divine authority because the the Written law, the Torah.
The Talmud ("look at") carries the Mishnah and the Gemara, the rabbinic debates on the Mishnah. There are basically two Talmuds: the Yerushalmi, or the Talmud of the Land of Israel, doubtless edited in Tiberias within the Galilee round 300-four hundred C.E., and the Babylonian Talmud or Bavli, composed in Babylon round 500-600 C.E.. both discussed the Mishnah and its scriptural groundwork in the Torah, but the Bavli joined Torah and Mishnah collectively more completely and was greater expansive. Jews for centuries have, for this reason, approached the Written legislation, the Torah, by way of the Oral law, and most peculiarly through the Bavli.
The rabbinic texts contain these sorts of types of writings:
Halakhah ("going," "running") - Jewish law as expounded by using the Talmudic sages
Haggadah (or Aggadah) - non-criminal substances including sermons, moral and ethical guideline, and folklore.
The six orders of the Mishnah are:
1. Zera'im ("seeds") offers with laws concerning agriculture, carries eleven tractates together with one on blessings and prayers.
2. Mo'ed ("season") carries twelve tractates about the fairs and the sabbath, together with a dialogue of what's regarded work prohibited on sabbath.
3. Nashim ("girls") addresses laws of marriage and divorce and has seven tractates.
four. Nezikin ("damages") has ten tractates concerned with civil legislations.
5. Kodashim ("sanctities") discusses the sacrifices and choices of the Temple in eleven tractates.
6. Tohoroth ("purities") has twelve tractates dealing with ritual purity.
Information Systems Security Architecture Professional (ISSAP) boot camp
Information Systems Security Architecture Professional (ISSAP) Exam Questions
Information Systems Security Architecture Professional (ISSAP) cheat sheet
Information Systems Security Architecture Professional (ISSAP) Actual Questions
Information Systems Security Architecture Professional (ISSAP) Latest Topics
Information Systems Security Architecture Professional (ISSAP) Exam dumps
Information Systems Security Architecture Professional (ISSAP) Test Prep
Information Systems Security Architecture Professional (ISSAP) Cheatsheet
Information Systems Security Architecture Professional (ISSAP) cheat sheet
What are the requirements to apply for refund?
In case, you fail the exam you can send your failing scoresheet by email to support and get the new exam in replacement or refund. You can further check requirements and details at https://killexams.com/pass-guarantee
You bet, Killexams is fully legit together with fully reputable. There are several functions that makes killexams.com unique and legitimized. It provides up to par and completely valid exam dumps made up of real exams questions and answers. Price is nominal as compared to most of the services online. The questions and answers are up-to-date on usual basis together with most recent brain dumps. Killexams account structure and products delivery is rather fast. Computer file downloading is normally unlimited and incredibly fast. Support is available via Livechat and Netmail. These are the features that makes killexams.com a robust website that offer exam dumps with real exams questions.
ISSAP - Information Systems Security Architecture Professional (ISSAP) PDF Dumps
ISSAP - Information Systems Security Architecture Professional (ISSAP) Free PDF
ISSAP - Information Systems Security Architecture Professional (ISSAP) learning
ISSAP - Information Systems Security Architecture Professional (ISSAP) exam success
ISSAP - Information Systems Security Architecture Professional (ISSAP) book
ISSAP - Information Systems Security Architecture Professional (ISSAP) tricks
ISSAP - Information Systems Security Architecture Professional (ISSAP) Free PDF
ISSAP - Information Systems Security Architecture Professional (ISSAP) Cheatsheet
ISSAP - Information Systems Security Architecture Professional (ISSAP) study help
ISSAP - Information Systems Security Architecture Professional (ISSAP) guide
ISSAP - Information Systems Security Architecture Professional (ISSAP) PDF Download
ISSAP - Information Systems Security Architecture Professional (ISSAP) PDF Download
ISSAP - Information Systems Security Architecture Professional (ISSAP) PDF Dumps
ISSAP - Information Systems Security Architecture Professional (ISSAP) testing
ISSAP - Information Systems Security Architecture Professional (ISSAP) braindumps
ISSAP - Information Systems Security Architecture Professional (ISSAP) Exam Braindumps
ISSAP - Information Systems Security Architecture Professional (ISSAP) study help
ISSAP - Information Systems Security Architecture Professional (ISSAP) exam format
ISSAP - Information Systems Security Architecture Professional (ISSAP) Exam Questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) information search
ISSAP - Information Systems Security Architecture Professional (ISSAP) testing
ISSAP - Information Systems Security Architecture Professional (ISSAP) Question Bank
ISSAP - Information Systems Security Architecture Professional (ISSAP) guide
ISSAP - Information Systems Security Architecture Professional (ISSAP) Practice Questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) braindumps
ISSAP - Information Systems Security Architecture Professional (ISSAP) Study Guide
ISSAP - Information Systems Security Architecture Professional (ISSAP) Exam Questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) outline
ISSAP - Information Systems Security Architecture Professional (ISSAP) testing
ISSAP - Information Systems Security Architecture Professional (ISSAP) exam syllabus
ISSAP - Information Systems Security Architecture Professional (ISSAP) Cheatsheet
ISSAP - Information Systems Security Architecture Professional (ISSAP) information hunger
ISSAP - Information Systems Security Architecture Professional (ISSAP) real questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) Exam Questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) course outline
ISSAP - Information Systems Security Architecture Professional (ISSAP) teaching
ISSAP - Information Systems Security Architecture Professional (ISSAP) Exam Questions
ISSAP - Information Systems Security Architecture Professional (ISSAP) outline
There are several Questions and Answers provider in the market claiming that they provide Real Exam Questions, Braindumps, Practice Tests, Study Guides, cheat sheet and many other names, but most of them are re-sellers that do not update their contents frequently. Killexams.com is best website of Year 2023 that understands the issue candidates face when they spend their time studying obsolete contents taken from free pdf download sites or reseller sites. That is why killexams update Exam Questions and Answers with the same frequency as they are updated in Real Test. Exam Dumps provided by killexams.com are Reliable, Up-to-date and validated by Certified Professionals. They maintain Question Bank of valid Questions that is kept up-to-date by checking update on daily basis.
If you want to Pass your Exam Fast with improvement in your knowledge about latest course contents and topics, We recommend to Download PDF Exam Questions from killexams.com and get ready for actual exam. When you feel that you should register for Premium Version, Just choose visit killexams.com and register, you will receive your Username/Password in your Email within 5 to 10 minutes. All the future updates and changes in Questions and Answers will be provided in your Download Account. You can download Premium Exam Dumps files as many times as you want, There is no limit.
Killexams.com has provided VCE Practice Test Software to Practice your Exam by Taking Test Frequently. It asks the Real Exam Questions and Marks Your Progress. You can take test as many times as you want. There is no limit. It will make your test prep very fast and effective. When you start getting 100% Marks with complete Pool of Questions, you will be ready to take Actual Test. Go register for Test in Test Center and Enjoy your Success.
Below are some important links for test taking candidates
Medical Exams
Financial Exams
Language Exams
Entrance Tests
Healthcare Exams
Quality Assurance Exams
Project Management Exams
Teacher Qualification Exams
Banking Exams
Request an Exam
Search Any Exam